If you are reasonably involved with internet services every day, you undoubtedly have heard about multi-factor authentication (MFA). If not, don’t worry, you will. Cybercrimes are on the rise, and their damage costs are predicted to achieve the impressive mark of $6 trillion by the end of 2021 [1]. Poor user practices, weak passwords, and lost/stolen user credentials are in the top 8 leading causes of ransomware attacks reported by managed service providers in 2020 [2]. One of the most devastating cyberattacks nowadays is the ransomware attack, which hijacks access to data and other resources in an organization until a ransom fee is paid (usually a very high amount).
Since an overwhelming portion of cyberattacks is associated with issues involving identity and access management (IAM), MFA has the potential of serving as a robust mitigation mechanism. Simply put: you should be using MFA, if not already.
However, at least three questions might be asked when someone hears about MFA for the first time: 1) What is authentication? 2) What is a factor in the context of authentication? 3) What is multi-factor authentication?
Breaking Down MFA
According to NIST, authentication is the process that verifies the identity of a user, process, or device, often as a prerequisite to allowing access to a system’s resources [3]. More specifically, digital authentication is the process of determining the validity of one or more authenticators used to claim a digital identity [4]. An authenticator is something the claimant possesses and controls (typically a cryptographic module or password) that is used to authenticate the claimant’s identity. An authenticator is also known as a token [5].
An authentication factor is a concrete instance of authentication. It typically refers to the method through which one will support a given identity claim. The most common example of an authentication factor is password authentication: whenever someone claims an identity (typically with a username), a password must also be informed to verify that identity.
Credit card holders are required to inform their pin code to prove their identity as well as owners of smartphones are often required to scan their face and/or fingerprint. So there is clearly more than one method for verifying an identity claim.
Indeed, authentication factors are organized into three main types:
- Something you know: a piece of information that a user has memorized and can be retrieved at any time. This includes a password, a personal identification number (pin), an answer for a pre-selected security question, an answer for randomly selected security questions (such as “What mortgage company you used for refinancing your house?”), and other mechanisms associated with information that (hopefully) only the intended user would know.
- Something you have: a piece of information that is provided by a physical device carried by the user. This is often done via security tokens that can store cryptographic keys, certificates, biometric information, and/or generate random codes, smartcards, and other mechanisms associated with information that only the intended user would have.
- Something you are: a piece of information provided by a device that can read a physical and unique characteristic of the user. This is known as biometrics – metrics from the human body – and can be very useful for authentication purposes. Smartphone users are familiar with fingerprint scans and facial recognition. Biometric devices are associated with information that only the intended user can provide just by being that user.
Other types of authentication factors might include:
- Somebody you know [6]: a type of vouching, that is, a peer-level authentication process when one user assists another user’s authentication.
- Something you process [7]: a type of formula-based authentication in which a password is composed of a set of characters, values, and operators, which are used in conjunction with random inputs to compute a result that is used for authentication.
- Somewhere you are [8]: a piece of information associated with the user’s location, such as GPS coordinates, IP, and MAC addresses.
- Something you do [9]: a piece of information associated with user’s behavior patterns while speaking, typing, gestures, among others.
However, the first three types those most commonly associated with MFA. In fact, the NIST Digital Identity Guidelines: Authentication and Lifecycle Management [4], only refers to something you know, something you have, and something you are as types of authentication factors.
An authentication system that requires only one authentication factor is known as single-factor authentication (SFA) [10]. When someone logs in to their social media account and all it takes to authenticate that person is a username (identity claim) and a password (what you know as a support of the identity claim), then SFA is in place. If, in addition to providing their password, the user receives a code via short message service (SMS) and must confirm that code in order to complete the authentication (what you have, a cellphone, as a support of the identity claim), then a second factor of authentication is in place. Combining two factors for authentication purposes is known as two-factor authentication (2FA).
Multi-factor is a characteristic of an authentication system or an authenticator that requires more than one distinct authentication factor for successful authentication. MFA can be performed using a single authenticator that provides more than one factor or a combination of authenticators that provide different factors.
The notion of factors should not be confused with the notion of steps, as remarked by Yuriy [11]. While factors refer to an action in the system, a step is a user-specific action. Yuriy explains that when someone must use a password and a security key (in a physical device) to authenticate, then 2FA in two steps is in place. However, if all a user has to do to authenticate is to touch a biometric sensor of a device equipped with a security key, then a 2FA is still in place (something you are + something you have) while authentication occurs in a single step. Thus FIDO2’s passwordless solution [12] is 2FA in one step while FIDO U2F [13] using passwords is 2FA in two steps.
MFA in Practice
Some of the most popular apps and services offer some form of MFA. For instance, LinkedIn allows their users to turn on two-step verification and choose if they will user an authenticator app or a phone number as a second authentication step.
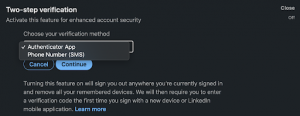
Two-step verification settings on LinkedIn
If the user chooses Authenticator App, LinkedIn will request the installation and configuration of Microsoft Authenticator or another authenticator app the user prefers.